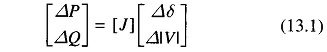Power System Security Analysis:
Power System Security Analysis can be broken down into two major functions that are carried out in an operations control centre:
- Security assessment, and
- Security control.
The former gives the security level of the system operating state. The latter determines the appropriate security constrained scheduling required to optimally attain the target security level.
The security functions in an EMS can be executed in ‘real time’ and ‘study’ modes. Real time application functions have a particular need for computing speed and reliability.
The static security level of a power system is characterised by the presence or otherwise of emergency operating conditions (limit violations) in its actual (pre-contingency) or potential (post-contingency) operating states. Power System Security Analysis assessment is the process by which any such violations are detected.
System assessment involves Two Functions:
- System monitoring and
- Contingency analysis.
System monitoring provides the operator of the power system with pertinent up-to-date information on the current conditions of the power system. In its simplest form, this just detects violations in the actual system operating state. Contingency analysis is much more demanding and normally performed in three distinct states, i.e. contingency definition, selection and evaluation. Contingency definition gives the list of contingencies to be processed whose probability of occurrence is high. This list, which is usually large, is in terms of network changes, i.e. branch and/or injection outages. These contingencies are ranked in rough order of severity employing contingency selection algorithms to shorten the list Limited accuracy results are required, therefore an approximate (linear) system model is utilized for speed. Contingency evaluation is then performed (using AC power flow) on the successive individual cases in decreasing order of severity. The evaluation process is continued up to the point where no post-contingency violations are encountered. Hence, the purpose of contingency analysis is to identify the list of contingencies that, if occur, would create violations in system operating states. They are ranked in order of severity.
The second major security function, security control, allows operating personnel to change the power system operation in the event that a contingency analysis program predicts a serious problem, should a certain outage occur. Normally the security control is achieved through SCO (security constrained optimization) program.
Modelling for Contingency Analysis:
The power system limits of most interest in contingency analysis are those on line flows and bus voltages. Since these are soft limits, limited-accuracy models and solutions are justified. The most fundamental approximate load flow model is the NR model.
The DC load flow model in its incremental version is normally preferred.
This model assumes voltages to remain constant after contingencies. However, this is not true for weak systems. The utility has to prespecify whether it wants to monitor post-contingency “steady-state” conditions immediately after the outage (system inertial response) or after the automatic controls. (governor, AGC, ED) have responded. Depending upon this decision, different participation factors are used to allocate the MW generation among the remaining units. The reactive problem tends to be more non-linear and voltages are also influenced by active power flows.
FDLF is normally the best for this purpose since its Jacobian matrix is constant and single-line outages can be modelled using the matrix inversion lemma.
The model often used is
Contingency Selection:
There are two main approaches:
Direct methods: These involve screening and direct ranking of contingency cases. They monitor the appropriate post-contingent quantities (flows, voltages). The severity measure is often a performance index.
Indirect methods: These give the values of the contingency case severity indices for ranking, without calculating the monitored contingent quantities directly.
Simulation of line outage is more complex than a generator outage, since line outage results in a change in system configurations. The Inverse Matrix Modification Lemma (IMML) or ‘compensation’ method is used throughout the contingency analysis field. The IMML helps in calculating the effects of network changes due to contingencies, without reconstructing and refactorizing or inverting the base case network matrix. It is also possible to achieve computational economy by getting only local solutions by calculating the inverse elements in the vicinity of the contingencies. The question is how far one should go. Some form of sensitivity analysis may be used.
The problem of studying hundreds of possible outages becomes very difficult to solve if it is desired to present the results quickly so that corrective actions can be taken. One of the simplest ways of obtaining a quick calculation of possible overloads is to use network sensitivity factors. These factors show the approximate change in line flows for changes in generation on the network configuration and are derived from the DC load flow. They are of two types:
- Generation shift distribution factors
- Line outage distribution factors
In a practical situation when a contingency causing emergency occurs, control action to alleviate limit violations is always taken, if such a capability exists and a protective system permits time to do so.
The security control function (which is normally achieved by SCO) responds to each insecure contingency case (as obtained by contingency analysis), usually in decreasing order of severity by:
- Rescheduling the pre-contingency operating state to alleviate the emergency resulting from the contingency, and/or
- Developing a post-contingency control strategy that will eliminate the emergency, or
- Taking no action, on the basis that post-contingency emergency is small and/or probability of its occurrence is very low.
A specific security control function, then, is designed to
- Operate in real time or study mode
- Schedule active or reactive power controls or both
- Achieve a defined security level
- Minimize a defined operational objective
Only a small proportion of work on optimal power flow (OPF) has taken into account the security constraints. The most successful applications have been to the security constrained MW dispatch OPF sub-problem. The contingency-constrained voltage/var rescheduling problem, as of the writing of this text, still remains to be solved to a satisfactory degree.
The total number of contingency constraints imposed on SCO is enormous. The SCO or contingency constrained OPF problem is solved with or without first optimizing with respect to the base case (pre-contingency) constraints. The general procedure adopted is as follows:
- Contingency analysis is carried out and cases with violations or near violations are identified.
- The SCO problem is solved.
- The rescheduling in Step 1 might have created new violations, and therefore Step 1 should be repeated till no violations exist.
Hence, SCO represents a potentially massive additional computing effort. An excellent comprehensive overview of various available methods is presented by Stott et. al.
There is still great potential for further improvement in Power System Security Analysis control. Better problem formulations, theory, computer solution methods and implementation techniques are required.